UPDATE 1500 06/01/26 : Ransom has been extended (So i suspect MMH will pay something) As most Kiwis will know by now (and if not, hope you’ve had a good off the grid holiday), ManageMyHealth got ransomed. Long story short, a dodgy overseas group found a “hole” in the MMH system, and exploited it, allowing […]
Server Upgrade : LSI and lots (for me) storage
Well that was fun. I was running 2 “Servers” for home use, one being a Gen 10 HP Microserver, and the other an old desktop i5 6500 system (see here). Then I obtained a Dell R730 rackmount, with 4x 4TB SATA drives. Those drives ended up in the HP. But I found that when […]
GTR vs Georgia State Police – 270KMPH!
Those that know me, know I love my Nissans, but in this video, the GTR driver was a moron and deserved to get busted. But the cops driving… wow… impressive. He stuck with the GTR and survived.
My First Internet
My first foray into the internet started during my Amiga days, around the time that BBS’s we’re on the decline and the internet was becoming cheaper and more accessible to the masses. I had been running my BBS for a few years, and started to notice a decline in regular callers, and that other BBS’s […]
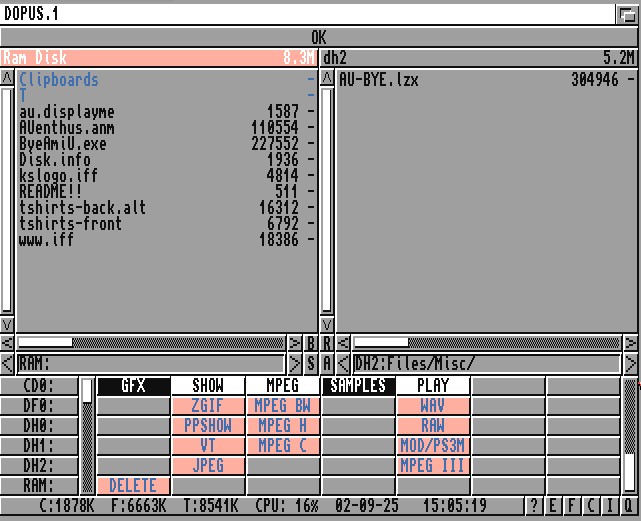
My Directory Opus Configuration
I loved Directory Opus. I have never found another file manager that even comes close. While I should like Directory Opus 5 onwards (inc the Windows ones), v4 was the bees knees for me. So I stuck with it. And here is my config file for you to obtain, use, and abuse. (Hosted on mega.nz) […]
Radio XPD is back!
Some of you may remember a number of years ago, I started a streaming “radio” station, playing Amiga related music. Well, after quite some downtime, it’s back! So feel free to tune in to some classic Amiga tunes and remixes, streaming 24/7 all the way from New Zealand. http://radio.xpd.co.nz:8000 or add the above URL […]